Our transaction monitoring tool offers a comprehensive, fully automated service designed for the financial sector and businesses seeking AML/CFT compliance. Each transaction is meticulously analyzed to ensure alignment with a customer’s risk profile and to identify any suspicious indicators. The rule editor and automated reporting functionality enhance productivity and enable smooth compliance. The module’s ability to identify similar alerts and detect cases further facilitates quality improvement over time.
Transaction monitoring
Why request a demo?
400+ requested demos already
Problems
we solve
Prevent financial crime, money laundering, and terrorist financing through regular monitoring and analysis of suspicious financial transactions. Regulatory requirements require continuous tracking of such activity throughout the lifespan of a customer relationship and timely reporting of suspicious behavior is crucial.
Why us?

Real-time
Detect suspicious behavior in real-time through continuous transaction monitoring. Block any transaction that exceeds your risk appetite, ensuring immediate action to mitigate potential risks.
Customizable
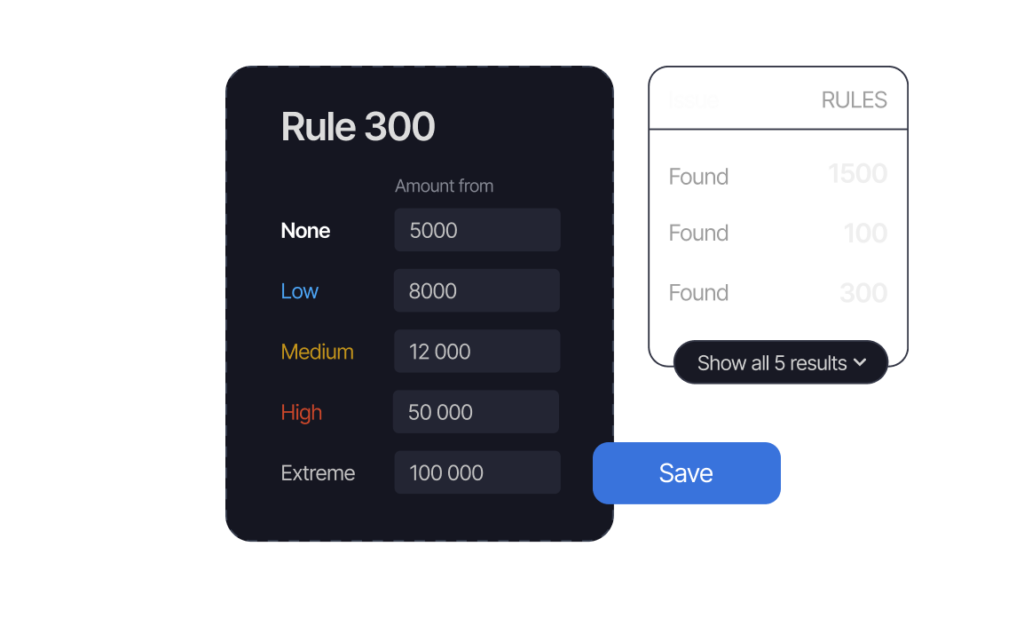
Build and customize your rule sets to meet your specific needs and regulatory requirements. Leverage the user-friendly interface to configure rules without the need for programming skills, ensuring flexibility and adaptability.

Efficient
Stay on top of your rules and scenario performance by eliminating inefficient ones. Efficient rule management enables effective monitoring and streamlines compliance efforts.
Protect your organization
Why request a demo?
FAQ
AML transaction monitoring solution is a system that uses analytics and automation to detect suspicious patterns of behavior associated with financial crime. Examples of such suspicious patterns of behavior include large transactions from high-risk countries, sudden changes in transaction value or volume, suspicious transactions involving individuals with certain profiles (e.g. politically exposed persons, or known criminals).
The solution can be used by banks, financial institutions, and other organizations seeking to comply with anti-money laundering (AML) regulations. The primary objective is to identify customer activity that may indicate money laundering. The solution also typically includes reporting and alerting functionality that sends alerts to the appropriate compliance personnel. There are two most commonly used types of transaction monitoring – real-time and retrospective – and we can offer both in our platform.
It helps financial institutions identify potential risks and take appropriate action to prevent financial crime and maintain the integrity of the financial system. Transaction monitoring helps identify and prevent fraud, money laundering and other financial crimes.
Rule-based monitoring involves setting up pre-defined rules to detect transactions that fall outside normal business practices. Another, Behaviour-Based Monitoring, involves analyzing patterns of behavior to identify anomalies or deviations from expected behavior. And peer group analysis involves comparing the transaction patterns of an individual or entity with those of a similar peer group. If an individual’s or entity’s transaction patterns deviate significantly from the peer group, this may indicate potential suspicious activity.
If you are planning to implement a transaction monitoring module in your organization, there are three main aspects you need to consider: data and system integration, transaction monitoring configuration, and defining the investigation process. Let’s look at each of these in more detail.
Data and systems integration refers to the process of identifying and connecting the data sources that will feed the transaction monitoring module. This can include internal systems such as core banking, CRM or accounting, as well as external sources such as third-party databases, APIs or web services. The complexity and effort of this step depends on the availability, quality and compatibility of the data sources.
Configuring transaction monitoring refers to the process of defining the rules and scenarios that will trigger alerts when suspicious or anomalous transactions are detected. This can include setting thresholds, parameters, weights and scores for different transaction types, customers or channels. The difficulty and accuracy of this step depends on the level of customisation and optimisation you wish to achieve.
Defining the investigation procedure refers to the process of defining the roles and responsibilities of staff who will handle alerts generated by the transaction monitoring module. This can include defining workflows, escalation paths, reporting formats and documentation standards. The challenge and efficiency of this step will depend on the skills, experience and availability of the staff involved.
The process of data integration for transaction monitoring is straightforward from a technical perspective, as we offer modern API methods to facilitate this. Of course, the success of data integration depends on the quality and governance of the client and transactional data being monitored.
If your data is well-structured and your IT staff are familiar with the applications your teams use, the integration will be easy. Sometimes, data quality issues that affect the organization may surface during the implementation of a transaction monitoring module. But we will assist you with data governance and quality for transaction monitoring during integration. We check and validate your data for various aspects, such as completeness, accuracy, consistency, timeliness, and provide you with suggestions and feedback for improvement.
To reduce the number of false positives, it is essential to fine-tune the transaction monitoring system according to the specific needs and characteristics of your organization and its risk exposure. This requires adjusting the thresholds, parameters, and scenarios that trigger alerts for suspicious transactions. Usually, this process involves at least several rounds of testing and tuning based on historical transactional data, with close collaboration between our experts and your AML staff.
The system also needs to be periodically tested and validated to maintain its accuracy and effectiveness. False positives can have negative consequences such as wasting resources and exposing your services to money laundering risks, so it is vital to optimize the transaction monitoring system to prevent unnecessary alerts and criminal abuse.

